Extending the lifetime of barrier coverage by adding sensors to a bottleneck region
One important application of wireless sensor networks (WSNs) is intruder detection for protection of a region of interest, and k-barrier coverage is...
One important application of wireless sensor networks (WSNs) is intruder detection for protection of a region of interest, and k-barrier coverage is...
A Wireless Sensor network is very exposed to different type of attacks and the most common one is the Sybil attack. A...
Smart home security control system has became indispensable in daily life. The design and development of a home security system, based on human face...
Wireless Sensor Networks are by its nature prone to various forms of security attacks. Authentication and secure communication have become the need of the...
VANET (Vehicle Ad-hoc Network) [1] is an emerging technology that enables the vehicles to communicate with each other. Nowadays, we see...
Mixed Flash and JavaScript content has become increasingly prevalent; its purveyance of dynamic features unique to each platform has popularized...
It is critical to monitor IT systems that are part of energy delivery system infrastructure. The problem with intrusion detection...
Mapping origin-destination (OD) network traffic is pivotal for network management and proactive security tasks. However, lack of sufficient flow-level measurements as well as potential...
The exponential growth and development in the wireless communication, Wireless communication technology gains an importance and can be used in...
Security of one-time password (OTP) is essential because nowadays most of the e-commerce transactions are performed with the help of this...
| Technology | Ph.D | M.Tech | M.S |
|---|---|---|---|
| Wireless Sensor Networks | 3 | 25 | 13 |
| Security | 5 | 28 | 18 |
| Mobile computing | 7 | 36 | 19 |
| Cognitive Radio Network | 4 | 42 | 16 |
| IOT | 9 | 19 | 13 |
| LTE | 6 | 21 | 19 |
| Manet | 2 | 27 | 21 |
| Open Flow | 3 | 14 | 24 |
| SDN | 11 | 13 | 26 |
| VANET | 14 | 36 | 18 |
| Vide Streaming | 2 | 4 | 7 |
| WBAN | 13 | 13 | 19 |
| Vertical Handover | 4 | 12 | 15 |
| D-D communication | 2 | 10 | 8 |
| Attacks | 32 | 59 | 42 |
| WIFI | 2 | 7 | 5 |
| Bluetooth | 1 | 2 | 4 |
| Social sensor network | 4 | 13 | 26 |
| Under water sensor network | 7 | 15 | 11 |
| Multicast | 1 | 19 | 7 |
| 5g,4g | 12 | 34 | 13 |
| IPv4,IPV6 | 16 | 42 | 19 |








































Wireless Body Area Networks
Wireless sensor and Actor networks
Wireless sensor and Actuator network
WiFi Mesh Networks
Virtual private network
Vascular Network
Sparse Vehicular Networks
Unicast
Two-Tier Femtocell Networks
Tolerant Military Networks
SIMO Networks
Social Media Networks
Software Defined Network
TCP Migration
Telecommunication Networks
Robotic Sensor Networks
Road Networks
Ring Networks
Multicast
Clos network
Mobile Ad hoc Network
Multicore CPUs
Multilayer Optical Network
Multimedia Wireless Networks
Vehicle Ad hoc Network VANET
MAC Layer Random Network
M2M Networks
LTE
Link State IP Networks
Inhomogeneous Sensor Networks
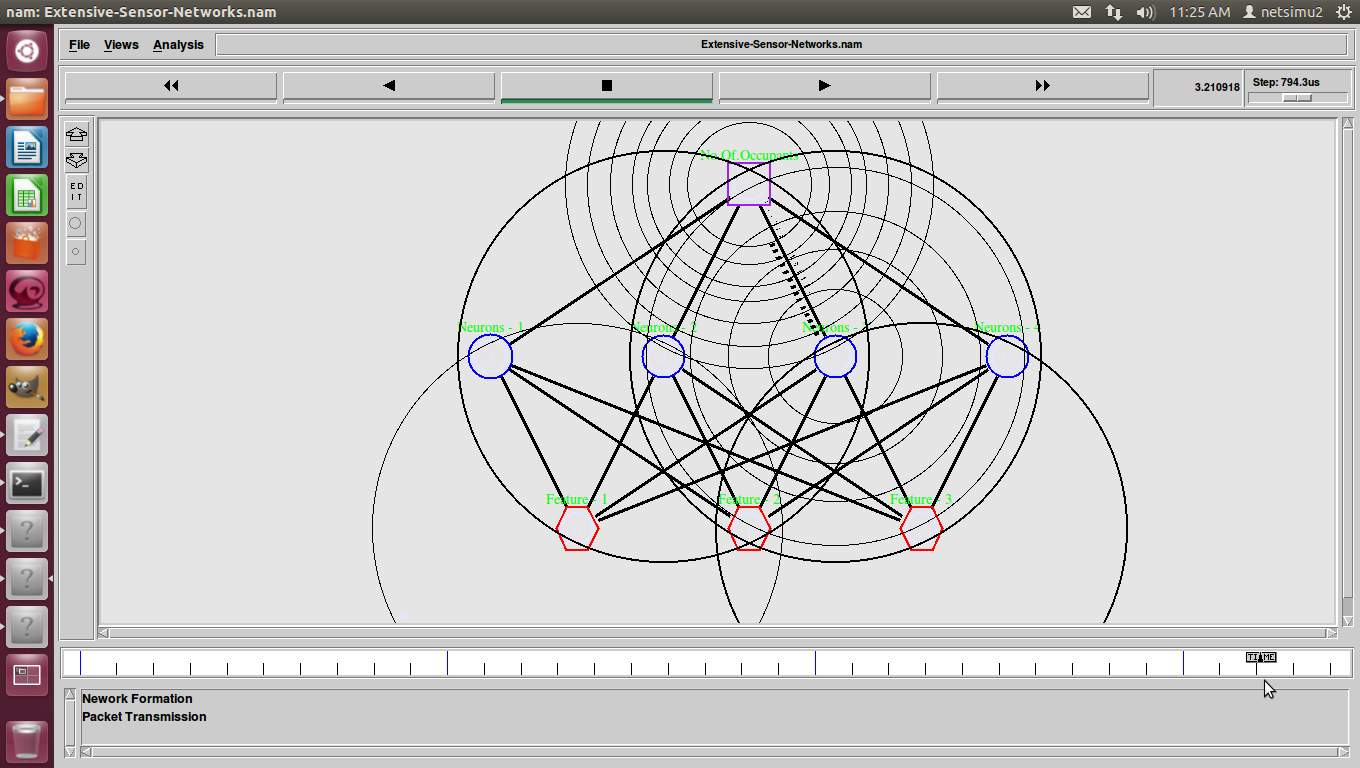
Extensive Sensor Networks
Fat-Tree-Based Networks
Cognitive Networks
Green Networking
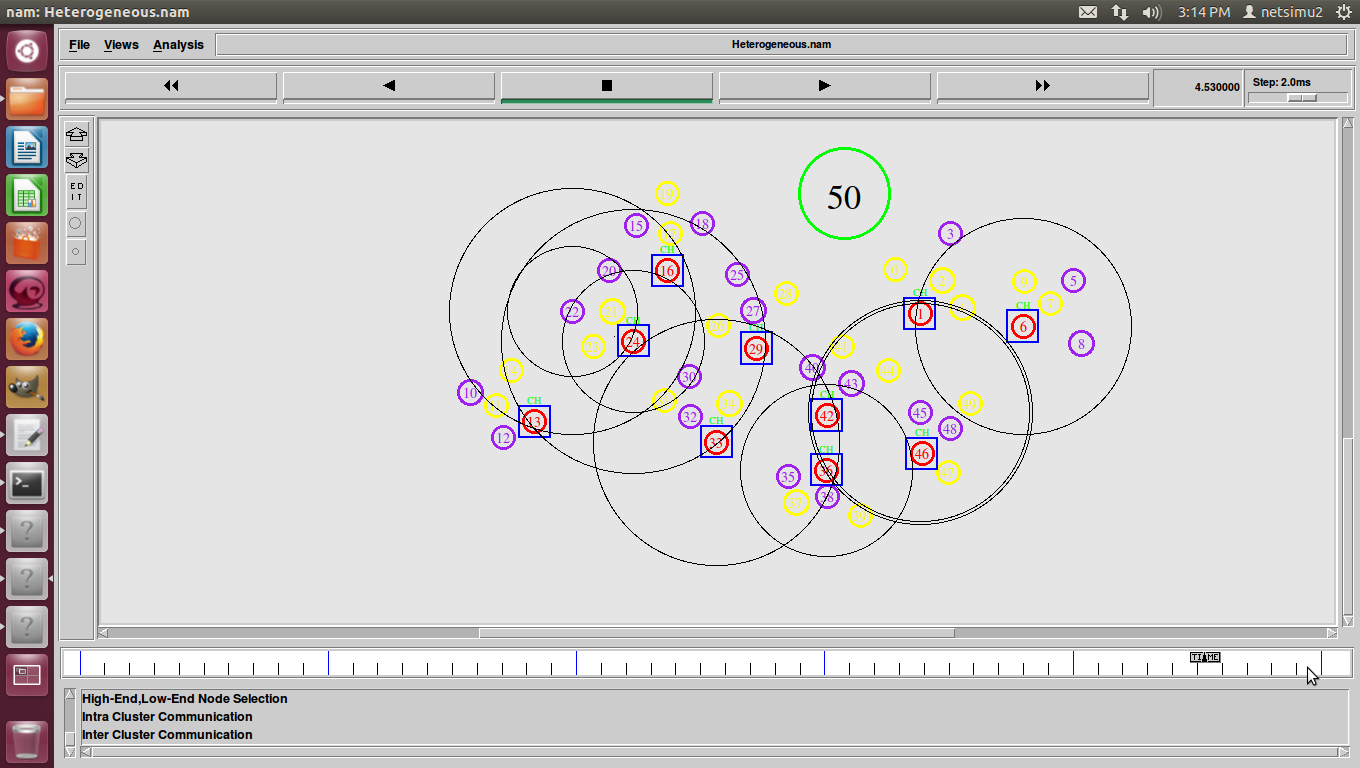
Heterogeneous Networks
Delay Tolerant Mobile Networks
Data Center Networks
Cognitive Radio Networks
Cooperative Learning in Networks
Cognitive Underlay Networks.
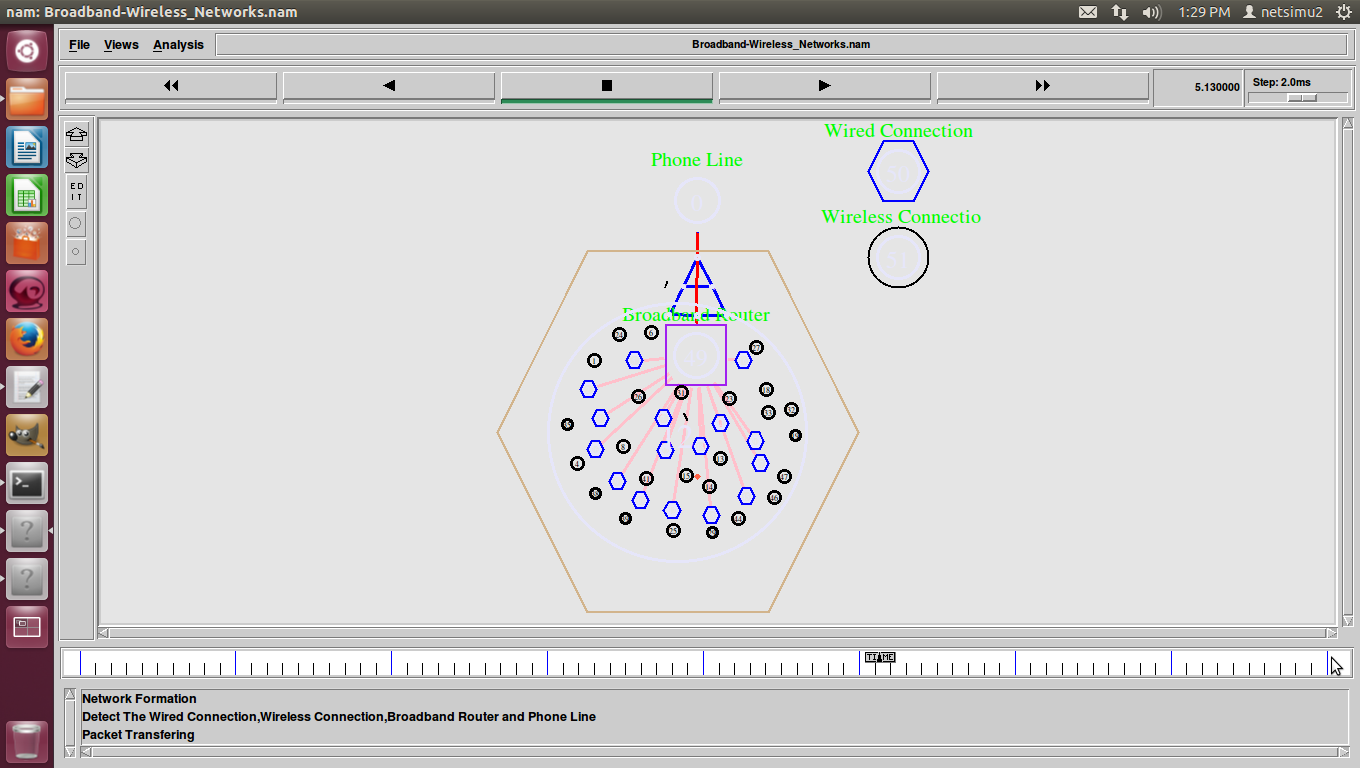
Broadband Wireless Networks
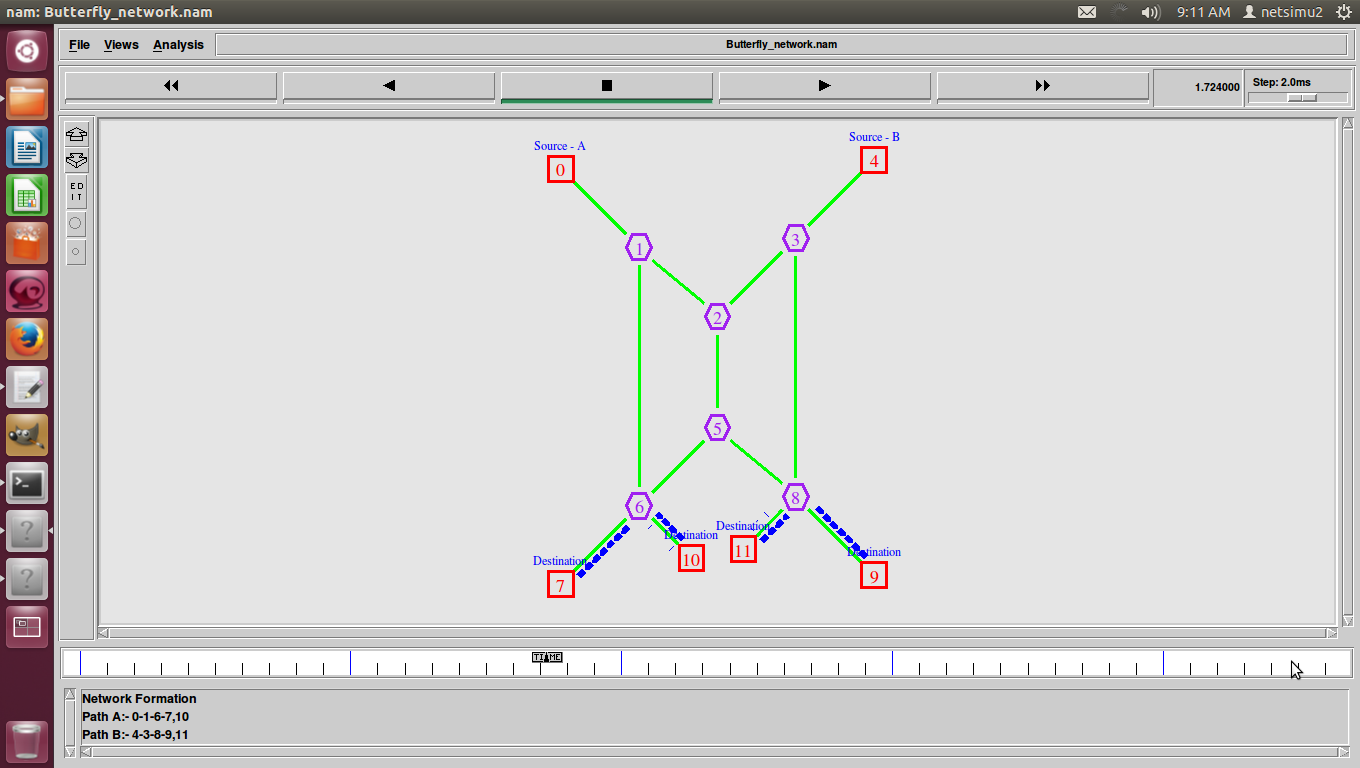
Butterfly Network
Cellular Networks
Cloud Radio Access Networks
Cluster-Based WSNs
Boolean Control Networks
Active Distribution Networks
Acoustic Communication Networks
5G Radio Access Networks
3D Sensor Networks
3D Sensor Networks
ALL Rights Reserved @ Network Simulator 2 | Ns2 Projects | Ns2 Research Projects | Network simulator 2 Projects.
