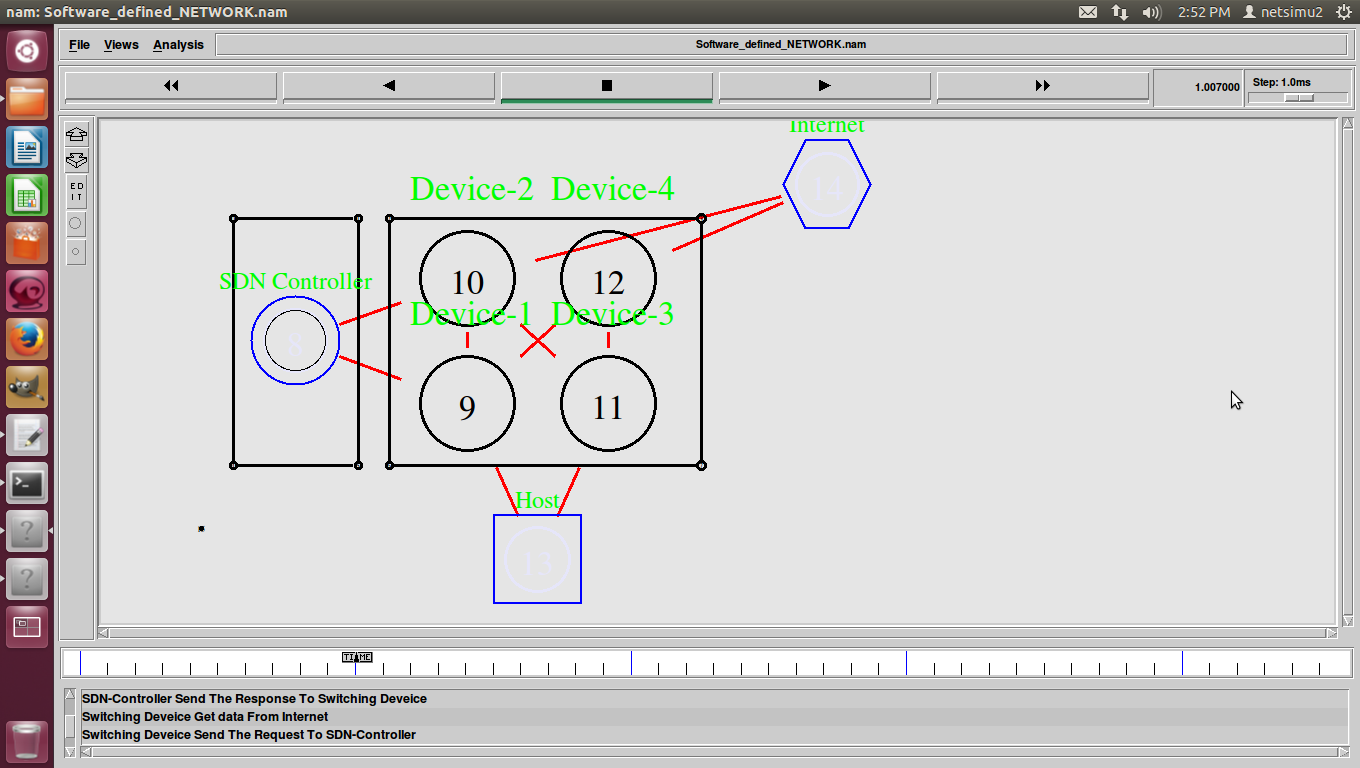
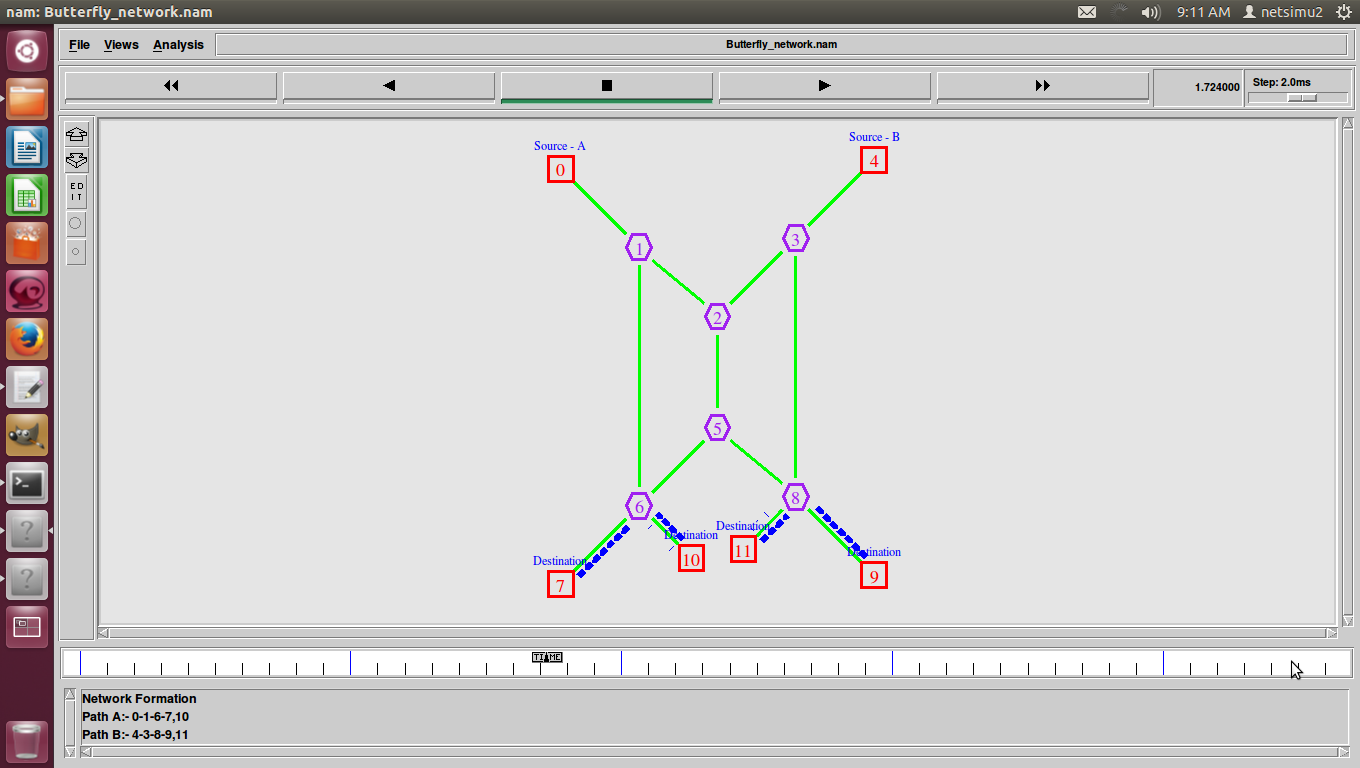
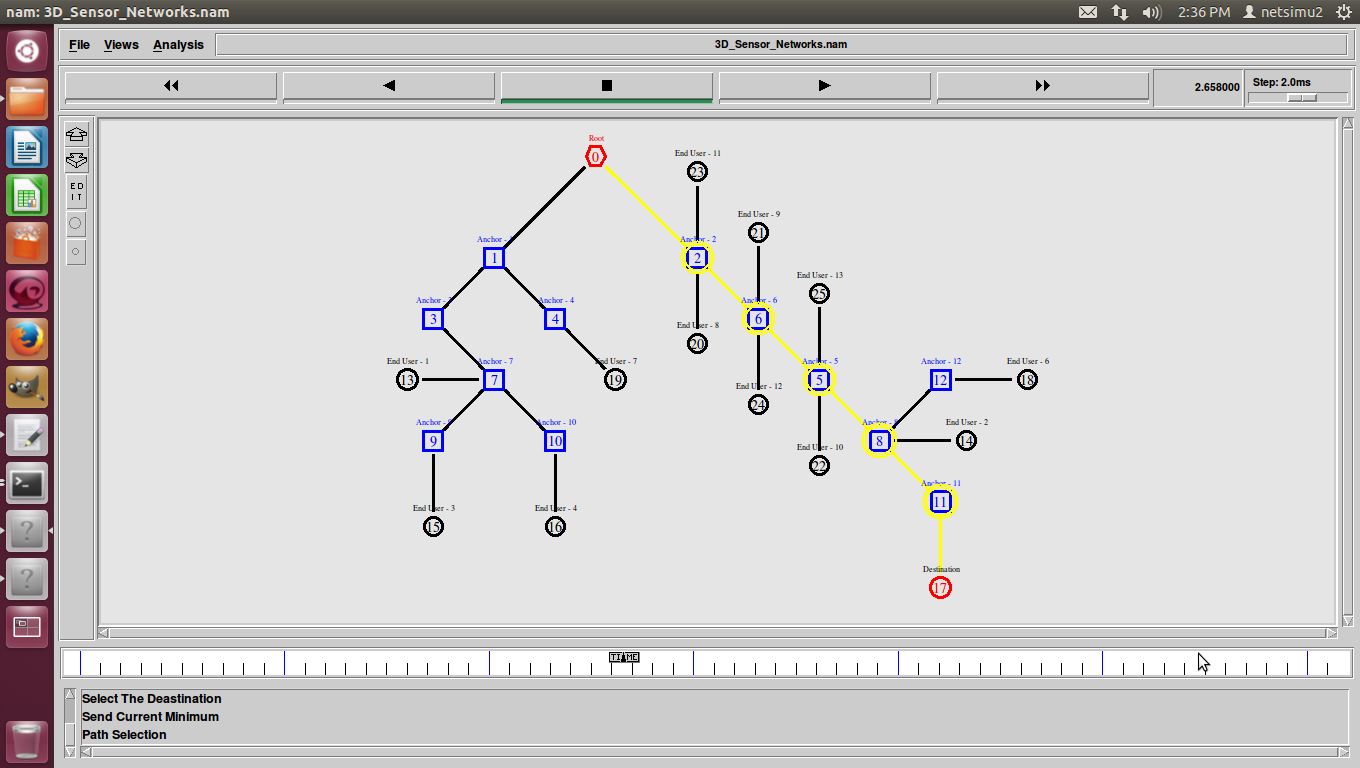
Towards an access control scheme for accessing flows in SDN
Sharing network resources with user groups, divisions, or even other companies in software defined networking promises better network utilization. Resource sharing is effectively realized...