A Secure Clustering in MANET through Direct Trust Evaluation Technique
Ad hoc network is a self organizing wireless network, made up of mobile nodes that act in both way as node and router....
Ad hoc network is a self organizing wireless network, made up of mobile nodes that act in both way as node and router....
Mobile malware attempts to evade detection during app analysis by mimicking security-sensitive behaviors of benign apps that provide similar functionality (e.g.,...
By extending the notion of minimum rank distance, this paper introduces two new relative code parameters of a linear code...
Although wireless sensor network applications are still at early stages of development in the industry, it is obvious that it will pervasively...
A mobile ad hoc network is a dynamic network of mobile hosts that does not have any centralized administration framework. Nodes in this network are self-organizing...
The purpose of this paper is to provide an overview of Aircraft Systems Information Security Protection (ASISP) from an FAA AVS perspective....
Large datasets of real network flows acquired from the Internet are an invaluable resource for the research community. Applications include network modelling and...
Security is the key concern for every system, network or application. Penetration Testing in Software engineering and System Security in Computer Networks are key areas in secure...
Public protection and disaster relief (PPDR) operations are increasingly more dependent on networks and data processing infrastructure. Incidents such as...
Intrusion Detection in a network is defined as identifying activities which violate security policies. Traditional Intrusion Detection Systems (IDSs) are centralized in nature where...
| Technology | Ph.D | M.Tech | M.S |
|---|---|---|---|
| Wireless Sensor Networks | 3 | 25 | 13 |
| Security | 5 | 28 | 18 |
| Mobile computing | 7 | 36 | 19 |
| Cognitive Radio Network | 4 | 42 | 16 |
| IOT | 9 | 19 | 13 |
| LTE | 6 | 21 | 19 |
| Manet | 2 | 27 | 21 |
| Open Flow | 3 | 14 | 24 |
| SDN | 11 | 13 | 26 |
| VANET | 14 | 36 | 18 |
| Vide Streaming | 2 | 4 | 7 |
| WBAN | 13 | 13 | 19 |
| Vertical Handover | 4 | 12 | 15 |
| D-D communication | 2 | 10 | 8 |
| Attacks | 32 | 59 | 42 |
| WIFI | 2 | 7 | 5 |
| Bluetooth | 1 | 2 | 4 |
| Social sensor network | 4 | 13 | 26 |
| Under water sensor network | 7 | 15 | 11 |
| Multicast | 1 | 19 | 7 |
| 5g,4g | 12 | 34 | 13 |
| IPv4,IPV6 | 16 | 42 | 19 |








































Wireless Body Area Networks
Wireless sensor and Actor networks
Wireless sensor and Actuator network
WiFi Mesh Networks
Virtual private network
Vascular Network
Sparse Vehicular Networks
Unicast
Two-Tier Femtocell Networks
Tolerant Military Networks
SIMO Networks
Social Media Networks
Software Defined Network
TCP Migration
Telecommunication Networks
Robotic Sensor Networks
Road Networks
Ring Networks
Multicast
Clos network
Mobile Ad hoc Network
Multicore CPUs
Multilayer Optical Network
Multimedia Wireless Networks
Vehicle Ad hoc Network VANET
MAC Layer Random Network
M2M Networks
LTE
Link State IP Networks
Inhomogeneous Sensor Networks
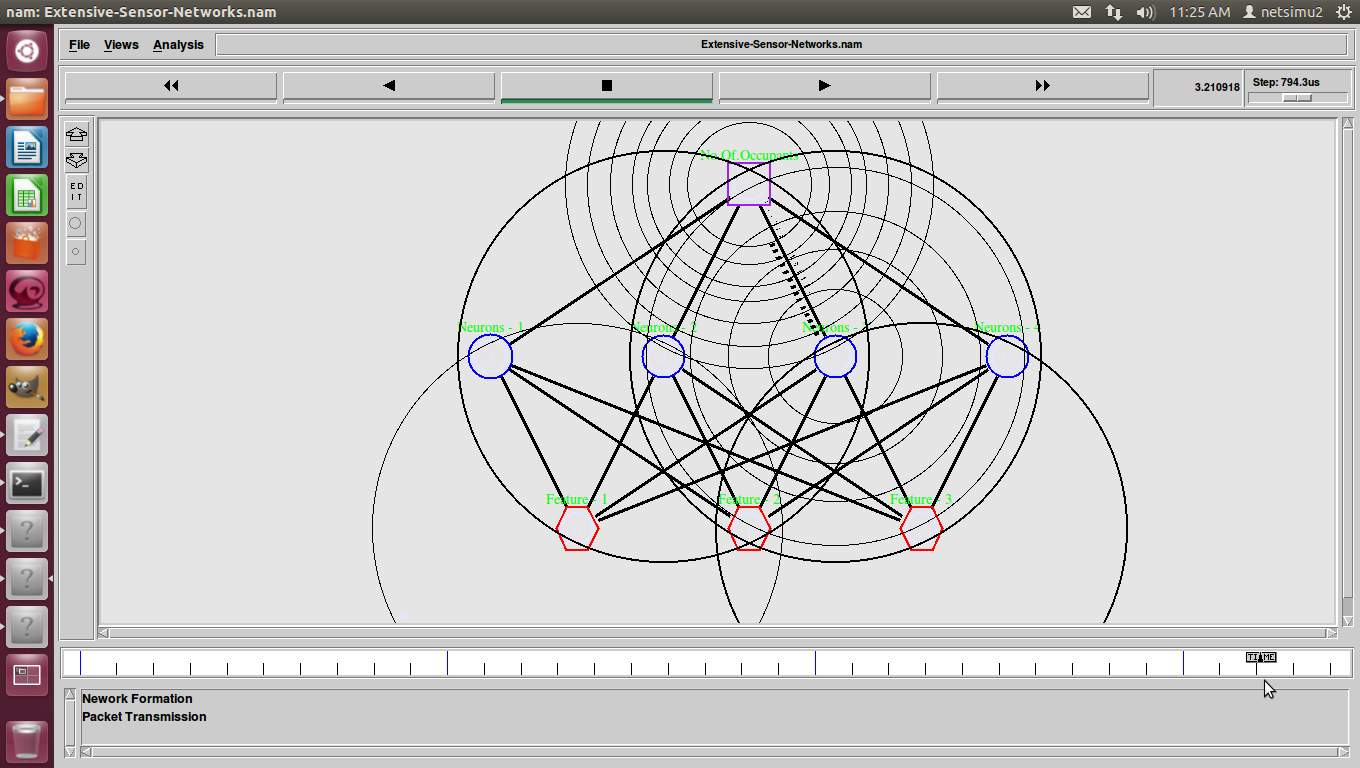
Extensive Sensor Networks
Fat-Tree-Based Networks
Cognitive Networks
Green Networking
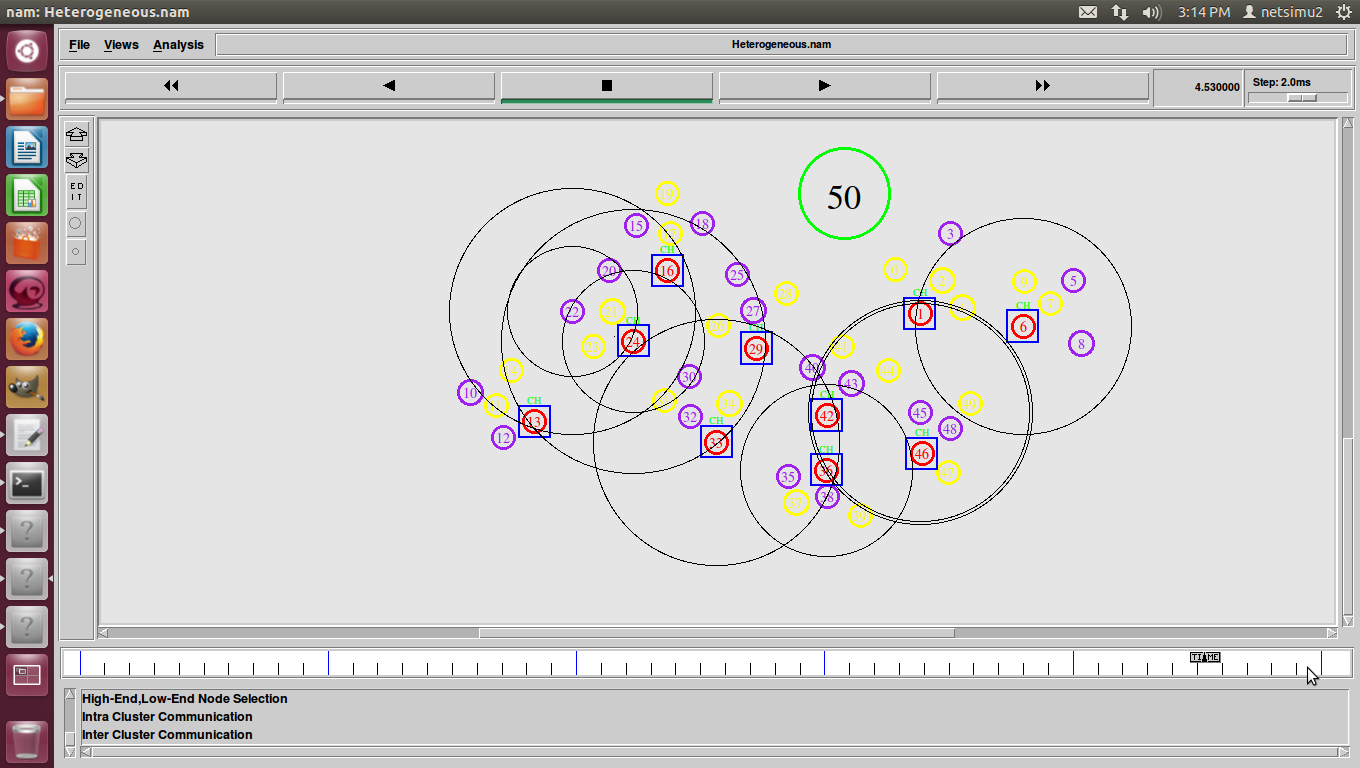
Heterogeneous Networks
Delay Tolerant Mobile Networks
Data Center Networks
Cognitive Radio Networks
Cooperative Learning in Networks
Cognitive Underlay Networks.
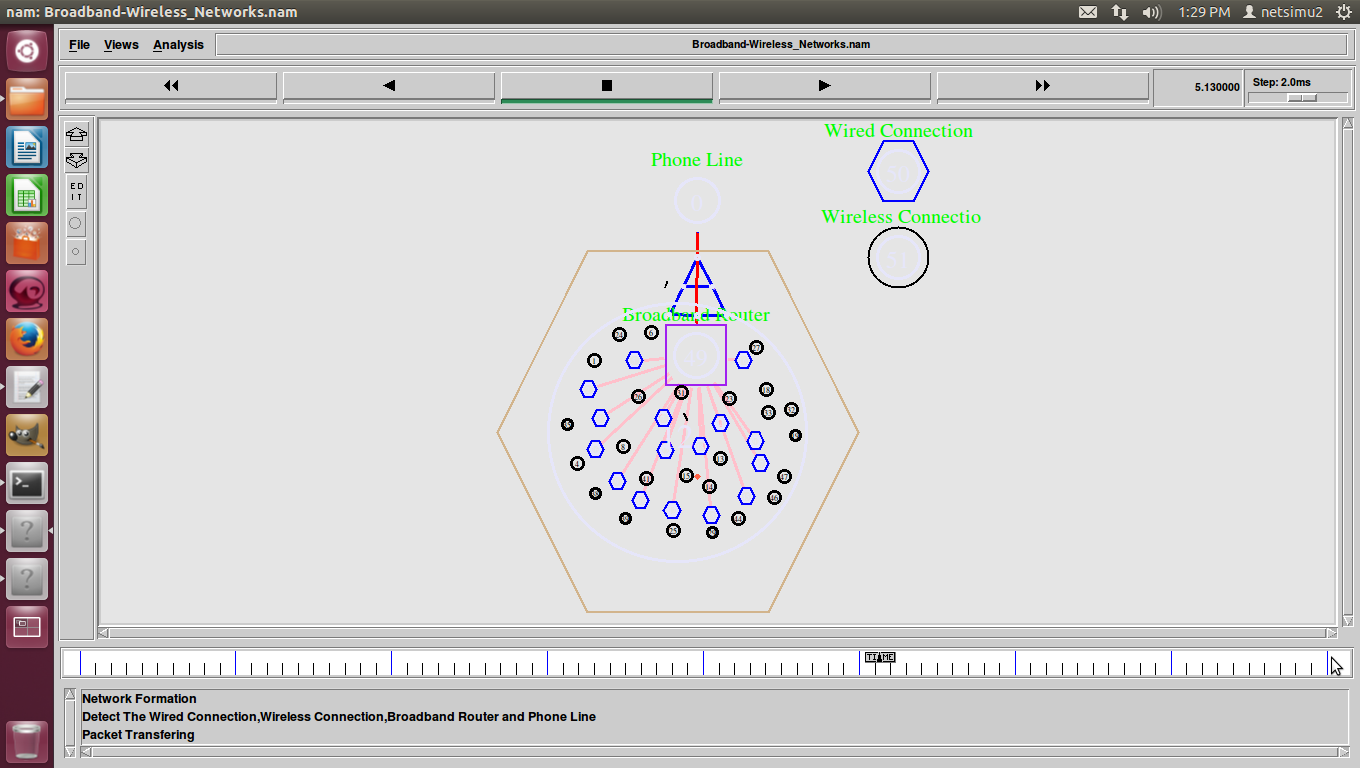
Broadband Wireless Networks
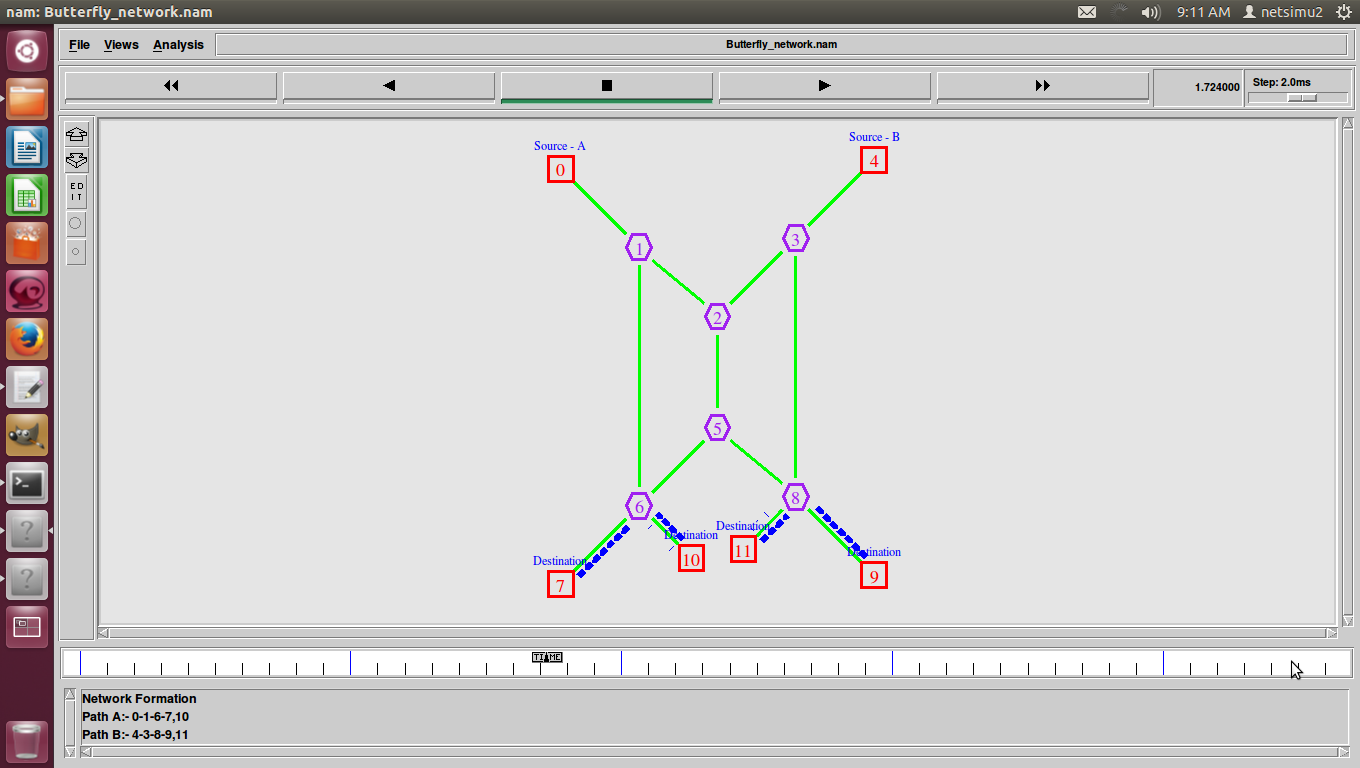
Butterfly Network
Cellular Networks
Cloud Radio Access Networks
Cluster-Based WSNs
Boolean Control Networks
Active Distribution Networks
Acoustic Communication Networks
5G Radio Access Networks
3D Sensor Networks
3D Sensor Networks
ALL Rights Reserved @ Network Simulator 2 | Ns2 Projects | Ns2 Research Projects | Network simulator 2 Projects.
