Detection of gray hole in MANET through cluster analysis
Mobile Ad-Hoc Networks are autonomous and decentralized wireless systems. MANETs consist of mobile nodes that are free in moving in and out...
Mobile Ad-Hoc Networks are autonomous and decentralized wireless systems. MANETs consist of mobile nodes that are free in moving in and out...
Advancements in wireless networking have initiated the idea of mobile computing, where the user does not have to be bound to a...
This chapter examines the problem of security assurance and conditional privacy preservation in vehicular communication applications. It introduces a novel security and privacy preserving...
Attack graphs show possible paths that an attacker can use to intrude into a target network and gain privileges through series of...
Computer security has become an important part of the day today’s life. Not only single computer systems but an extensive network of the computer...
Cloud computing is increasingly changing the landscape of computing, however, one of the main issues that is refraining potential customers...
The vulnerability of Cloud Computing Systems (CCSs) to Advanced Persistent Threats (APTs) is a significant concern to government and industry....
We build upon the clean-slate, holistic approach to the design of secure protocols for wireless ad-hocnetworks proposed in part one. We...
In this paper, we review the parallel and distributed optimization algorithms based on alternating direction method of multipliers (ADMM) for...
This study presents some of the most important checkpoints found in the deployment or migration projects for PACS (Picture Archiving...
| Technology | Ph.D | M.Tech | M.S |
|---|---|---|---|
| Wireless Sensor Networks | 3 | 25 | 13 |
| Security | 5 | 28 | 18 |
| Mobile computing | 7 | 36 | 19 |
| Cognitive Radio Network | 4 | 42 | 16 |
| IOT | 9 | 19 | 13 |
| LTE | 6 | 21 | 19 |
| Manet | 2 | 27 | 21 |
| Open Flow | 3 | 14 | 24 |
| SDN | 11 | 13 | 26 |
| VANET | 14 | 36 | 18 |
| Vide Streaming | 2 | 4 | 7 |
| WBAN | 13 | 13 | 19 |
| Vertical Handover | 4 | 12 | 15 |
| D-D communication | 2 | 10 | 8 |
| Attacks | 32 | 59 | 42 |
| WIFI | 2 | 7 | 5 |
| Bluetooth | 1 | 2 | 4 |
| Social sensor network | 4 | 13 | 26 |
| Under water sensor network | 7 | 15 | 11 |
| Multicast | 1 | 19 | 7 |
| 5g,4g | 12 | 34 | 13 |
| IPv4,IPV6 | 16 | 42 | 19 |








































Wireless Body Area Networks
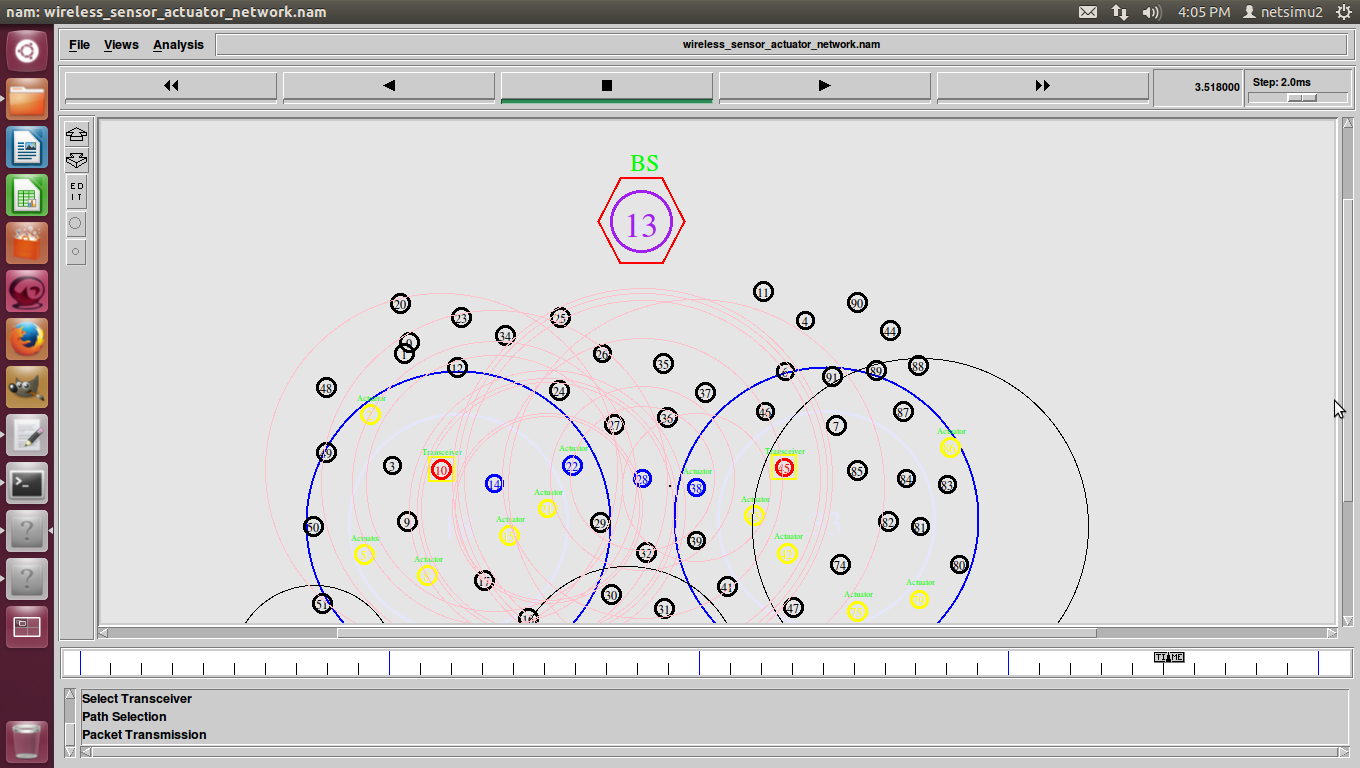
Wireless sensor and Actor networks
Wireless sensor and Actuator network
WiFi Mesh Networks
Virtual private network
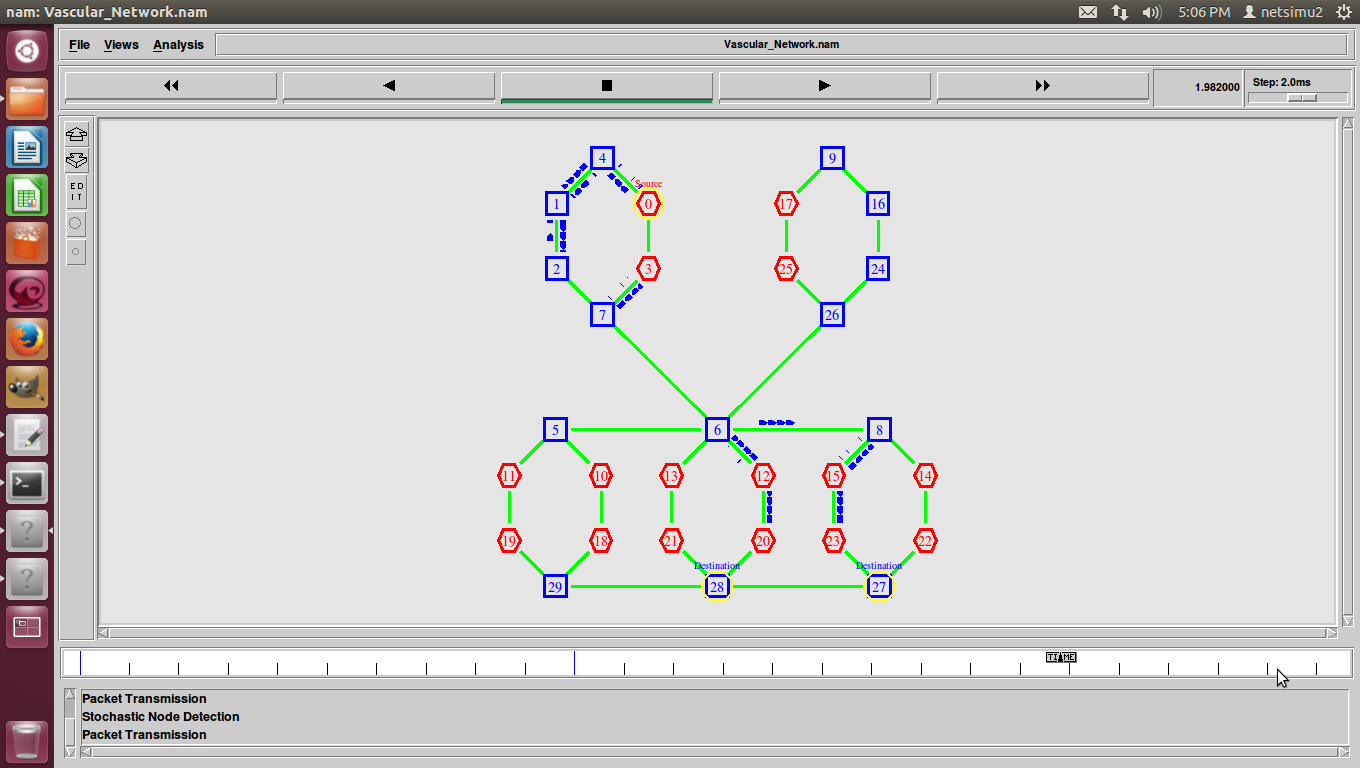
Vascular Network
Sparse Vehicular Networks
Unicast
Two-Tier Femtocell Networks
Tolerant Military Networks
SIMO Networks
Social Media Networks
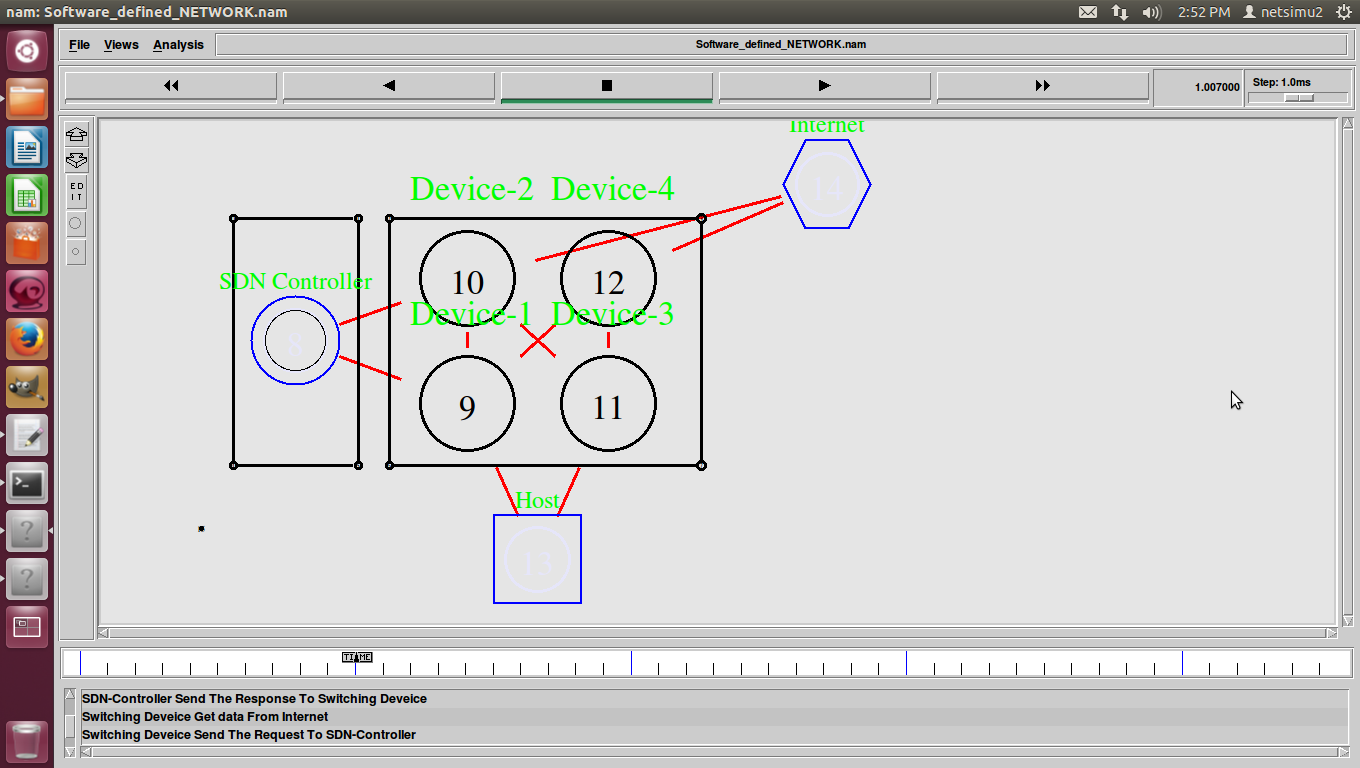
Software Defined Network
TCP Migration
Telecommunication Networks
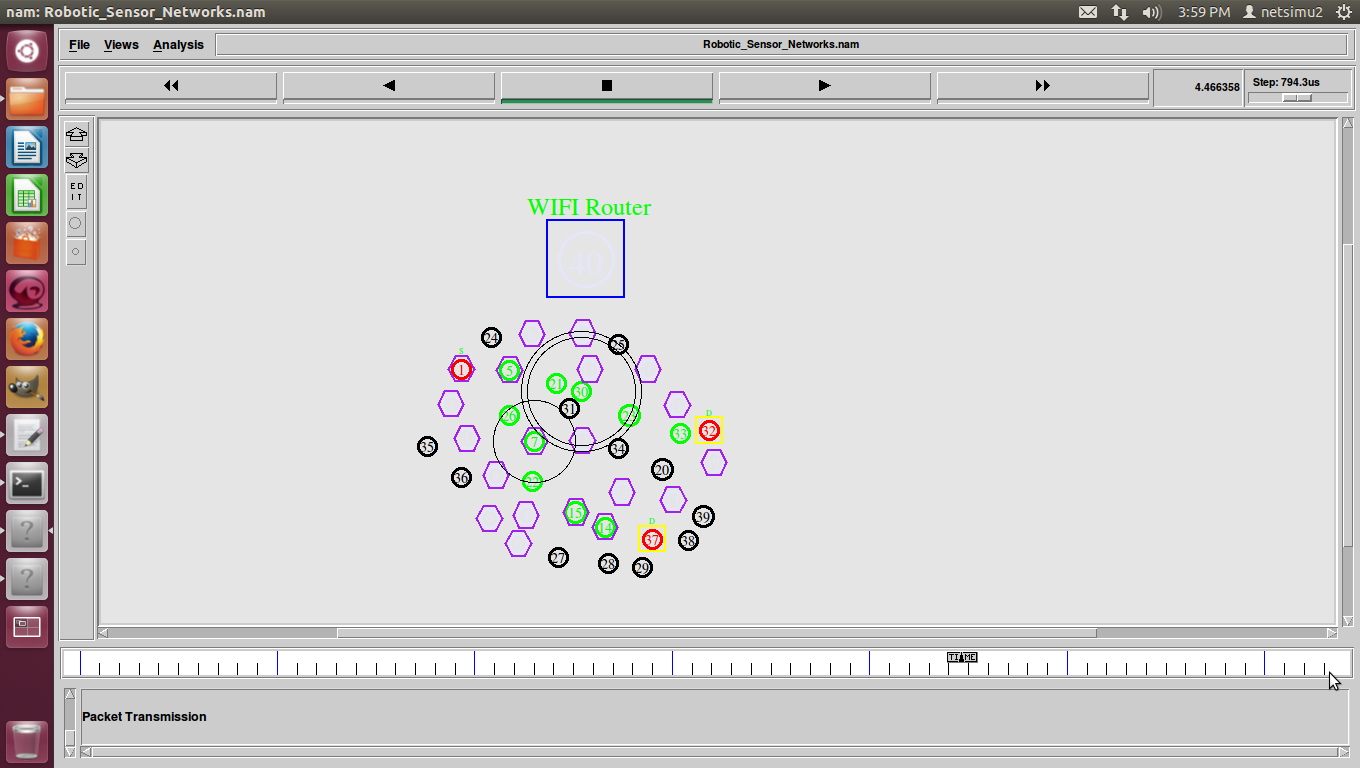
Robotic Sensor Networks
Road Networks
Ring Networks
Multicast
Clos network
Mobile Ad hoc Network
Multicore CPUs
Multilayer Optical Network
Multimedia Wireless Networks
Vehicle Ad hoc Network VANET
MAC Layer Random Network
M2M Networks
LTE
Link State IP Networks
Inhomogeneous Sensor Networks
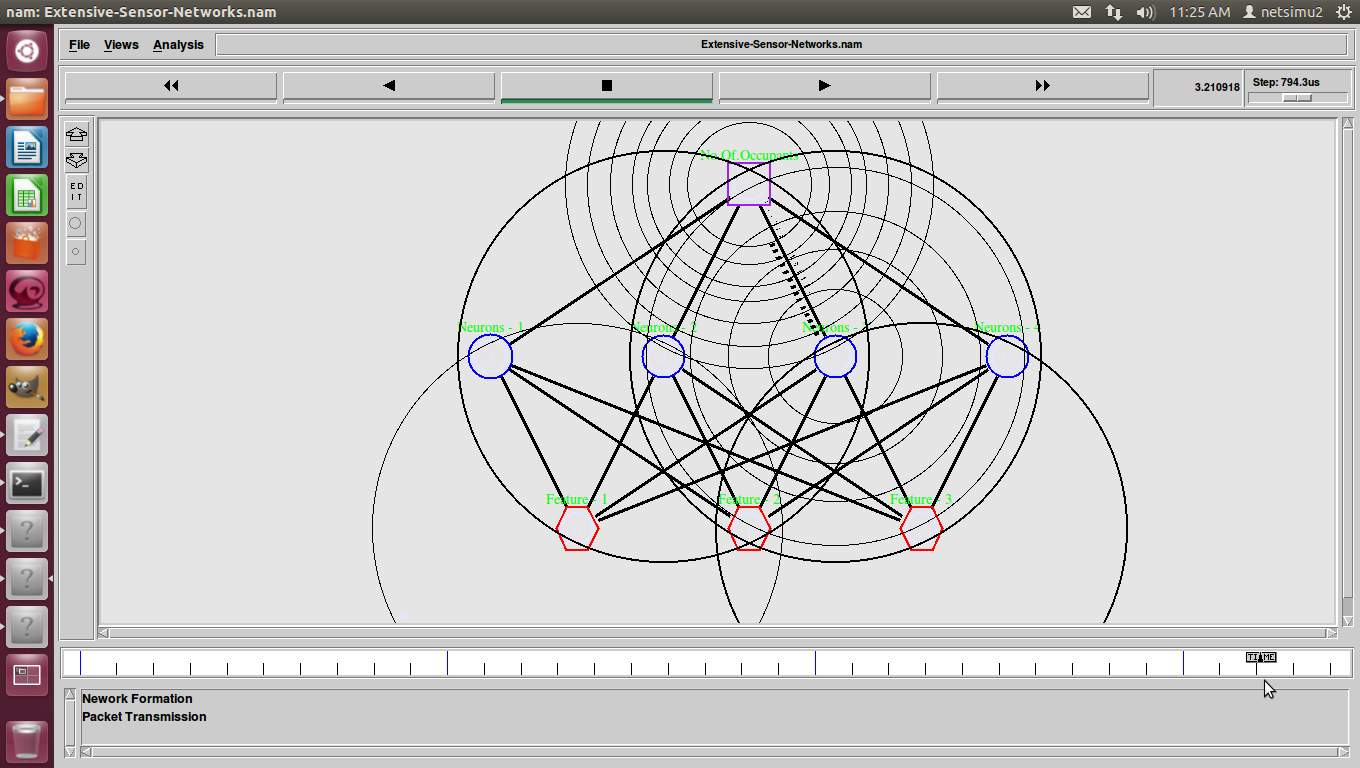
Extensive Sensor Networks
Fat-Tree-Based Networks
Cognitive Networks
Green Networking
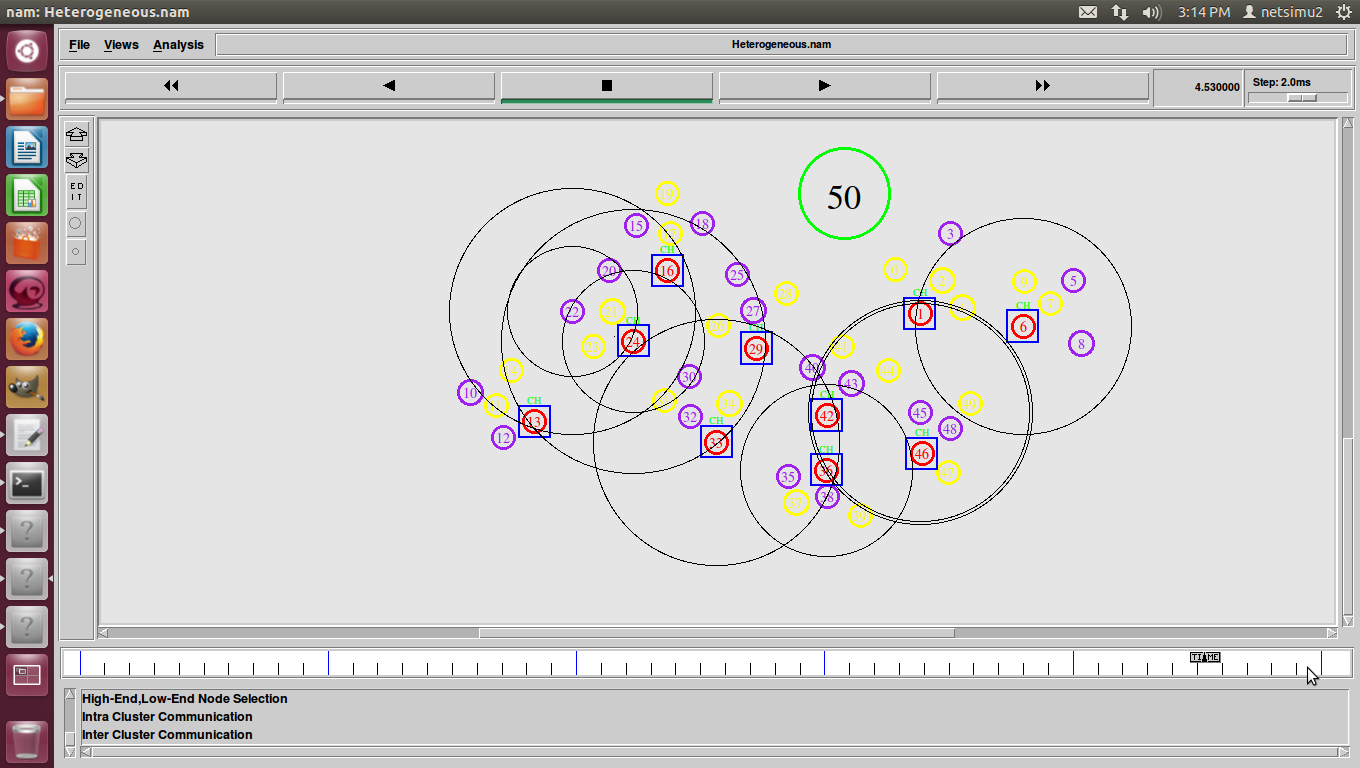
Heterogeneous Networks
Delay Tolerant Mobile Networks
Data Center Networks
Cognitive Radio Networks
Cooperative Learning in Networks
Cognitive Underlay Networks.
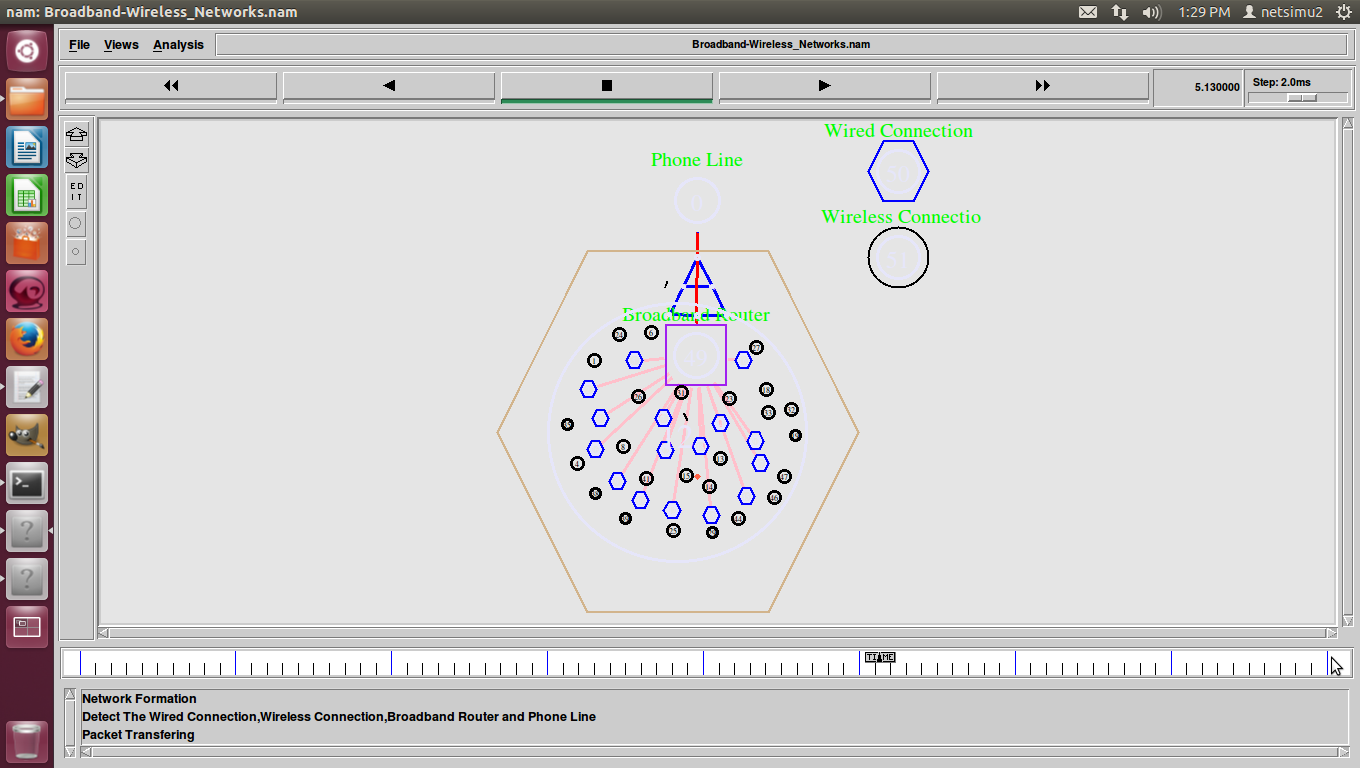
Broadband Wireless Networks
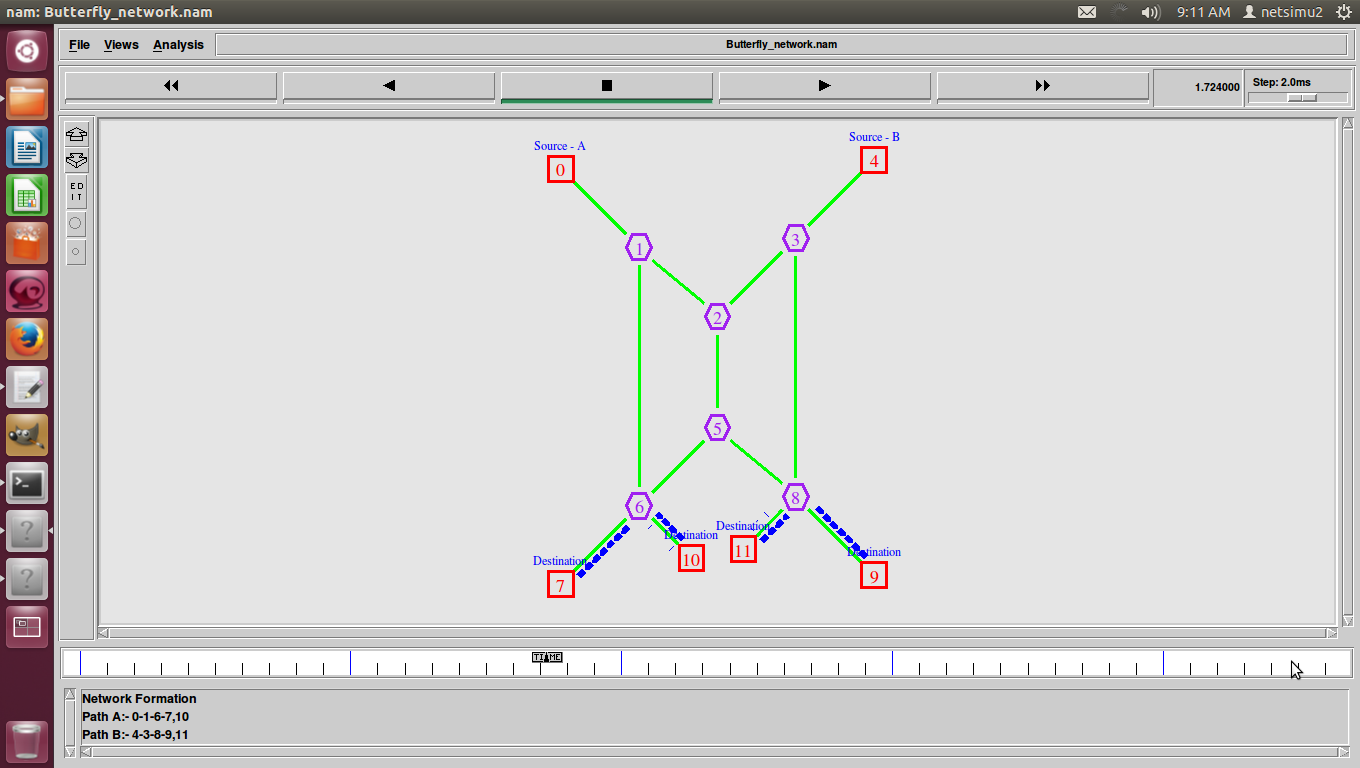
Butterfly Network
Cellular Networks
Cloud Radio Access Networks
Cluster-Based WSNs
Boolean Control Networks
Active Distribution Networks
Acoustic Communication Networks
5G Radio Access Networks
3D Sensor Networks
3D Sensor Networks
ALL Rights Reserved @ Network Simulator 2 | Ns2 Projects | Ns2 Research Projects | Network simulator 2 Projects.
