rsa ns2 – RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being also sent over an insecure network.
What is rsa?
- Ron Rivest, Adi Shamir, and also Leonard Adleman introduce a cryptographic algorithm.
- The RSA-algorithm is also based on the fact that there is no efficient way to factor very large numbers. Deducing an RSA-key, also therefore, requires an extraordinary amount of computer processing power and time.
Advantages of RSA-algorithm:
- Gives high speed also for encryption.
- Generating unknown also private keys.
- New applications can also add without updating the chip.
- Chip has SED algorithm and also all other features of classisSys.
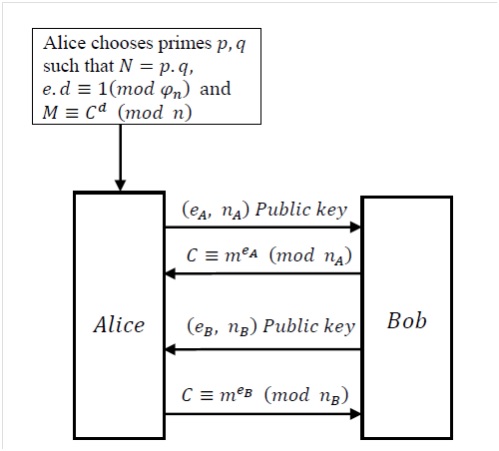
Procedure Involve in RSA-NS2 Projects

Sample RSA NS2 Code
proc rsa_encrypt {
input skey
} {
upvar $skey key
if {
[bitsize $key(n)] < [bitsize $input]
} {
error "keysize [bitsize $key(n)] must be greater than text [bitsize $input]/$input"
}
return [powm $input $key(e) $key(n)]
}
proc rsa_decrypt {
input skey
} { upvar $skey key
if {
[bitsize $key(n)] < [bitsize $input]
} {
error "keysize [bitsize $key(n)] must be greater than text [bitsize $input]/$input"
}
if {
!
} {
return [rsa_slow_decrypt $input key]
}
set m1 [powm $input [fdiv_r $key(d) [sub_ui $key(p) 1]] $key(p)]
set m2 [powm $input [fdiv_r $key(d) [sub_ui $key(q) 1]] $key(q)]
set h [sub $m2 $m1]
if {
[cmp_si $h 0] < 0
} {
set h [add $h $key(q)]
}
set h [fdiv_r [mul $key(u) $h] $key(q)]
set m [add $m1 [mul $h $key(p)]]
return $m
}
proc rsa_slow_decrypt {
input pkey
} {
upvar $pkey key
if {
[bitsize $key(n)] < [bitsize $input]
} {
error "keysize [bitsize $key(n)] must be greater than text [bitsize $input]/$input"
}
if {
[catch {
set ptext [powm $input $key(d) $key(n)]
}]
} {
puts "rsa_slow_decrypt: $input [hex $key(d)] [hex $key(n)]"
error "powm error"
}
return $ptext
}
proc pack_text {
ptext keylen
} {
while {
[string length $ptext] < ($keylen - 16)
} {
append ptext [binary format H* [::md5::md5 $ptext]]
}
if {
[string length $ptext] < $keylen
} {
set md5 [binary format H* [::md5::md5 $ptext]]
append ptext [string range $md5 0 [expr $keylen - [string length $ptext] - 1]]
}
binary scan $ptext H* hex
return [convert 0x$hex]
}
proc encrypt {
ptext pkey
} {
upvar $pkey key
set keylen [bytesize $key(n)]
set en [pack_text $ptext $keylen]
set en [rsa_encrypt $en key]
append ctext [hex $en]
set ctext [binary format H* $ctext]
return $ctext
}
Tweet